Amazon S3 inventory Pricing?
This article provides a general overview of AWS S3 Inventory Pricing, and also highlights a few details in general.
What is S3 Inventory?
- It’s one of the tools that are provided by S3 for aiding users to manage storage. It may be utilized for reporting & auditing the status of objects for requirements of regulatory, compliance, business & compliance types.
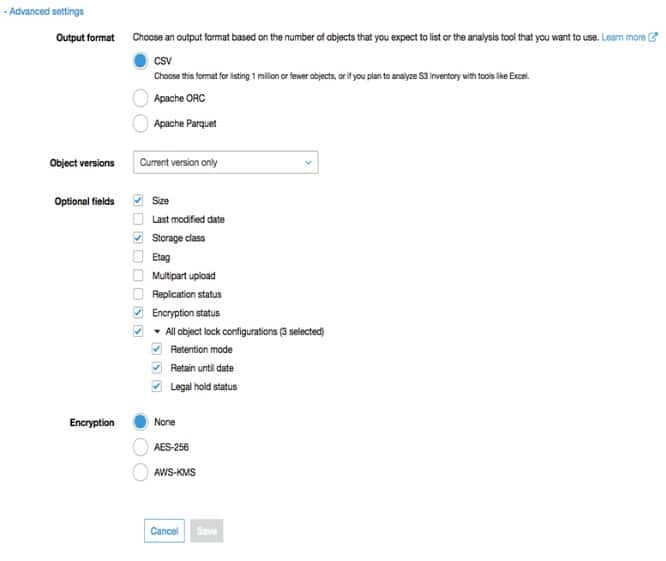
- S3 inventory offers output files of the following types: CSV, ORC or Parquet. Those output files will list objects along with their associated metadata every day/week for a specific shared prefix (or) an S3 bucket.
- Customers are even capable of reporting the Intelligent-Tiering access tier as a metadata field within their inventory reports free of charge.
It’s now possible for customers to utilize S3 Inventory for reporting every object that is stored in the S3 Intelligent-Tiering storage class. The newly created storage class has the following characteristics:
- Simplifies the reduction of costs on storage for both IT infrastructure managers & developers.
- Does not allow for loss of availability or performance.
- It gets the job done by storing objects in either 1 of the following access tiers:
> Tier optimized for Frequent access
> A less expensive tier optimized for Infrequent access.
It is now possible for users to rely on S3 Inventory to view Intelligent-Tiering objects in any Region. To set and configure your S3 Inventory, you can use one of the following:
- S3 Management Console.
- API
- CLI
- SDK
Charges will be allocated by storing objects in S3 buckets, depending on the following:
- Size of the objects.
- Monthly period of storing the objects.
- Chosen storage class (Glacier, and Glacier Deep Archive, Standard and Standard – Infrequent Access, Intelligent-Tiering, One Zone – Infrequent Access, and RRS).
Charges are incurred every month for automation/monitoring for every object which gets stored in Intelligent-Tiering class. Also, moving objects in between access tiers & monitoring access patterns.
- Lifecycle rules for moving your data into whatever storage class you choose, as well as COPY and PUT will get per-request ingest fees.
- Let the transition or ingest cost be taken into consideration prior to the act of moving objects into whatever storage class you choose.
All the costs referred to below are considered with US-East-2(Ohio) region.
- Charges incurred for Storage management features such as analytics, object tagging & S3 inventory that is enabled on your account’s buckets.
- S3 Storage Management will be priced according to every feature.
> S3 Inventory————————————$0.0025 per million objects listed
> S3 Analytics Storage Class Analysis———-$0.10 per million objects monitored/month
> S3 Object Tagging——————————$0.01 per 10,000 tags/month - All your files that get generated using the S3 Inventory/S3 Storage-Class-Analysis-exports will be stored in one of the selected S3 buckets. Those files will also undergo S3 Standard storage charges.
| Storage Types | Storage pricing |
|---|---|
| S3 Standard - General purpose storage for any type of data, typically used for frequently accessed data | |
| First 50 TB / Month | $0.023 per GB |
| Next 450 TB / Month | $0.022 per GB |
| Over 500 TB / Month | $0.021 per GB |
| S3 Intelligent - Tiering * - Automatic cost savings for data with unknown or changing access patterns | |
| Frequent Access Tier, First 50 TB / Month | $0.023 per GB |
| Frequent Access Tier, Next 450 TB / Month | $0.022 per GB |
| Frequent Access Tier, Over 500 TB / Month | $0.021 per GB |
| Infrequent Access Tier, All Storage / Month | $0.0125 per GB |
| Monitoring and Automation, All Storage / Month | $0.0025 per 1,000 objects |
| S3 Standard - Infrequent Access * - For long lived but infrequently accessed data that needs millisecond access | |
| All Storage / Month | $0.0125 per GB |
| S3 One Zone - Infrequent Access * - For re-createable infrequently accessed data that needs millisecond access | |
| All Storage / Month | $0.01 per GB |
| S3 Glacier ** - For long-term backups and archives with retrieval option from 1 minute to 12 hours | |
| All Storage / Month | $0.004 per GB |
| S3 Glacier Deep Archive ** - For long-term data archiving that is accessed once or twice in a year and can be restored within 12 hours | |
| All Storage / Month | $0.00099 per GB |
S3 Replication pricing
In S3 Same Region Replication & Cross-Region Replication, S3 charges are going to be paid for the following:
- Storage retrieval fees for Infrequent access.
- Storage in the selected destination S3 storage class.
- Replication PUT requests.
- Primary copy storage charges
The following are a few additional details incurred with S3 charges
- S3 Replication Time Control: The charges incurred for S3 Replication Metrics along with the Replication Time Control Data Transfer fee. The two will be billed at similar rates as those of the AWS CloudWatch custom metrics.
- CRR: The charges incurred for inter-region Data Transfers OUT from S3 to the destination region.
- Storage + PUT request for replicated copy Pricing: According to destination Region
- Inter-region data transfer Pricing: According to source Region.
> S3 Replication Time Control data transfer————$0.015 per GB - S3 Replication Time Control Data Transfer pricing will be the same for all AWS Regions.
- S3 Replication Time Control can be used in all commercial Regions excluding the ones below as of now.
> China (Beijing) Region
> China (Ningxia) Region
> GovCloud (US) Regions
Here are a few awesome resources on AWS Services:
- Cloudysave’s goal is to provide clear visibility about the spending and usage patterns to your Engineers and Ops teams.
- Have a quick look at CloudySave’s Cost calculator to estimate real-time AWS costs.