Asymmetric CMKs
Create your Asymmetric CMKs:
How to Create asymmetric CMKs using the console?
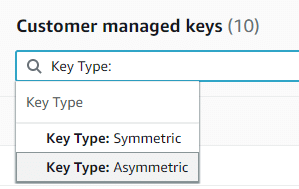
Asymmetric CMK – CMK Key Type Asymmetric
- Log into the Management Console then head directly to the KMS console using the following link https://console.aws.amazon.com/kms.
- For the sake of changing your current Region, you must refer to the Region selector from the top right.
- From navigation pane, select Customer managed keys.
- Click on Create key.
- For creating an asymmetric CMK, select the option Asymmetric from section Key type.
- For the sake of creating an asymmetric CMK for your process of public key encryption, you will need to select Encrypt and decrypt for the section of Key usage. Otherwise, for creating an asymmetric CMK to get the possibility to sign messages and then verify the signature, you will need to select the option Sign and verify from Key usage.
- Choose a particular specification which refers to Key spec to give to the asymmetric CMK.
- Click on Next.
- Enter a specific alias for the asymmetric CMK, which is not capable of staring with the prefix aws/.
- You can enter an optional description for the asymmetric CMK.
Type in a description which can describe what kind of data you’re planning to protect or which application you are planning to utilize using the asymmetric CMK. Avoid using the description format of AWS managed CMKs.
Asymmetric CMK – Asymmetric CMK Application Utilization
You are capable of either entering a description currently or you could just get it updated whenever you want, but make sure that the key state is not at Pending Deletion. For the sake of changing, adding or simply deleting the description of a customer managed CMK, you must start by editing the CMK using the Management Console or through utilizing UpdateKeyDescription operation.
- You can optionally enter a tag key and a tag value, and for adding even extra tags to your asymmetric CMK you will need to click on Add tag.
Upon adding tags to resources, AWS will generate a cost allocation report which includes usage and prices aggregated through tags.
- Click on Next.
- Choose which IAM users and roles are capable of administrating the asymmetric CMK.
Keep in Mind
IAM policies are capable of granting different IAM users and roles the permission to start managing the CMK.
- It is optional for you to choose to prevent the chosen IAM users and roles from having the ability to delete this asymmetric CMK, by going to the Key deletionsection located below the page and then clearing out the check box for Allow key administrators to delete this key.
- Click on Next.
- Choose which IAM users and roles are to be given the ability to utilize the asymmetric CMK for cryptographic operations.
Keep in mind
The root user will be given by default total permissions. Consequently, whichever IAM policies capable of granting users and roles permission will need to utilize the asymmetric CMK for the sake of performing cryptographic operations.
- You may also optionally provide access for different AWS accounts to be able to work with this asymmetric CMK for their cryptographic operations. For this to happen, you will need to head to the Other AWS accounts section located below of the page, select the option Add another AWS account and type in the required AWS account identification number of the needed external account. For adding even more external accounts, you must go over this same step.
Keep in Mind
For the sake of granting the possibility for principals in external accounts to work with the asymmetric CMK, the Administrators of external account will need to get IAM policies created which will grant them the required permissions.
- Select Next.
- Go over the key policy document which includes your choices of creation, and edit it if you’d like.
- Click on Finish in order to get the new asymmetric CMK created.
How to Create asymmetric CMKs using the AWS KMS API?
The CreateKey operation may be utilized for the creation of an asymmetric CMK.
The below examples have the AWS CLI, however it is possible to utilize a different language of supported programming.
Asymmetric CMK – Asymmetric CMK Decryption Algorithm
Upon creating an asymmetric CMK, you will have to set the CustomerMasterKeySpec parameter that will specify which keys are to be created. You will additionally need to set a KeyUsage value of either ENCRYPT_DECRYPT or SIGN_VERIFY, and those properties can no longer get changed upon the creation of your asymmetric CMK.
Asymmetric CMK – Asymmetric CMK Encryption Algorithm
The below is an example which utilizes the CreateKey operation for the sake of creating an asymmetric CMK having 4096-bit RSA keys made specifically for public key encryption.
$ aws kms create-key --customer-master-key-spec RSA_4096 --key-usage ENCRYPT_DECRYPT
{
"KeyMetadata": {
"KeyState": "Enabled",
"KeyId": "1234abcd-12ab-34cd-56ef-1234567890ab",
"CustomerMasterKeySpec": "RSA_4096",
"KeyManager": "CUSTOMER",
"Description": "",
"KeyUsage": "ENCRYPT_DECRYPT",
"Arn": "arn:aws:kms:us-west-2:111122223333:key/1234abcd-12ab-34cd-56ef-1234567890ab",
"CreationDate": 1569973196.214,
"EncryptionAlgorithms": [
"RSAES_OAEP_SHA_1",
"RSAES_OAEP_SHA_256"
],
"AWSAccountId": "111122223333",
"Origin": "AWS_KMS",
"Enabled": true
}
}
The below is an example command which tend to create an asymmetric CMK representing a pair of ECDSA keys that are utilized for the sign in and verification needs. An elliptic curve key pair may not be created for purposes of encryption and decryption.
$ aws kms create-key --customer-master-key-spec ECC_NIST_P521 --key-usage SIGN_VERIFY
{
"KeyMetadata": {
"KeyState": "Enabled",
"KeyId": "0987dcba-09fe-87dc-65ba-ab0987654321",
"CreationDate": 1570824817.837,
"Origin": "AWS_KMS",
"SigningAlgorithms": [
"ECDSA_SHA_512"
],
"Arn": "arn:aws:kms:us-west-2:111122223333:key/0987dcba-09fe-87dc-65ba-ab0987654321",
"AWSAccountId": "111122223333",
"CustomerMasterKeySpec": "ECC_NIST_P521",
"KeyManager": "CUSTOMER",
"Description": "",
"Enabled": true,
"KeyUsage": "SIGN_VERIFY"
}
}