What is Role Chaining?
One role can be assumed and then utilizing your temporary credentials for the sake of assuming another one, where it’s possible to go can from one session to another.
Passing session tags as one assumes a specific role, it will be possible to set the keys as transitive, in order to make sure that session tags are going to pass to successive sessions that go in a role chain.
Role tags are not capable of being set as transitive. In order to be able to pass those tags to successive sessions, you will to get them set as session tags.
In the below example you are going to discover the way of passing role tags, session tags and transitive tags into successive sessions taking place in a role chain.
- Below is a role chaining scenario, having IAM user’s access keys assuming a role named Role1 using the CLI. After this, the resulting session credentials are needed for the sake of assuming a 2nd role with the name Role2.
Later on, it’s possible to utilize 2nd session’s credentials for the sake of assuming a 3rd role with the name Role3. (3 separate procedures for those 3 requests). Every role is going to be tagged in IAM in the first place, where with every request there are more session tags being passed.
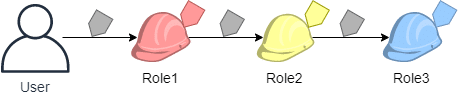
Session Tags for Chaining Roles – role chaining
- By chaining roles, tags from previous session will continue to the future sessions. assume-role CLI command: passing the tag as a session tag, then setting it as as transitive.
tag Star = 1 is passed as a session tag.
tag Heart = 1 gets attached to role and is going to be applied as a principal tag. Yet you will need Heart = 1 tag to get instantly passed to the 2nd or 3rd session, and for this to happen, you will have to add it as a session tag so that the resulting session’s principal tags contain those 2 tags, and specify them as transitive.
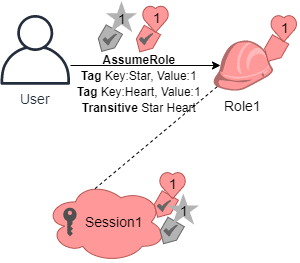
Session Tags for Chaining Roles – assume role
The request gets made through the below CLI command:
AssumeRole CLI Request example:
| aws sts assume-role \ |
| –role-arn arn:aws:iam::123456789012:role/Role1 \ |
| –role-session-name Session1 \ |
| –-tags Key=Star,Value=1 Key=Heart,Value=1 \ |
| –transitive-tag-keys Star Heart |
- Credentials will be used for assuming Role2.
Tag Sun = 2 will be attached to the 2nd role and applied as principal tag in 2nd session.
Heart & Star tags: Inherited from transitive session tags from 1st session.
Resulting principal tags from 2nd session: Sun = 2, Heart = 1, and Star = 1.
Heart and Star: still transitive.
Sun tag attached to Role2: not transitive, since not a session tag, which means that it is not going to be inherited for upcoming sessions.
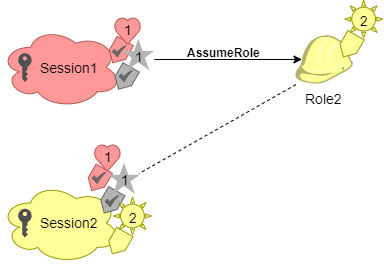
Session Tags for Chaining Roles – CLI request
2nd request is made with the below CLI command:
AssumeRole CLI Request Example:
| aws sts assume-role \ |
| –role-arn arn:aws:iam::123456789012:role/Role2 \ |
| –role-session-name Session2 |
- 2nd session credentials will be used for assuming Role3.
Principal tags of 3rd session result from any of role tags, random inherited transitive session tags, and new session tags.
Heart = 1 & Star = 1 tags from 2nd session: inherited from the 1st session transitive session tag.
The operation of passing the Heart = 3 session tag will not be able to succeed.
The role’s Star = 3 tag will be overridden by the Inherited Star = 1 session tag.
The 3rd session will get the role’s Lightning tag applied to it, without being specified as transitive.
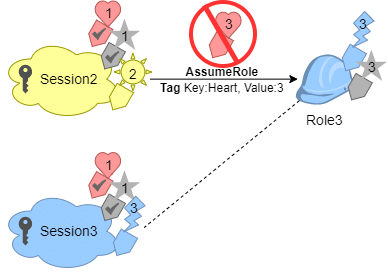
Session Tags for Chaining Roles – lightning
3rd request is made with the below CLI command:
AssumeRole CLI Request example:
| aws sts assume-role \ |
| –role-arn arn:aws:iam::123456789012:role/Role3 \ |
| –role-session-name Session3 |
How to Use Session Tags for ABAC?
ABAC: Authorization strategy which specifies permissions according to tag attributes.
For a company utilizing its corporate user identities with an SAML-based identity provider: It’ possible to get the SAML assertion configured for passing session tags to AWS. As soon as employees get federated into AWS, they will get attributes applied to the finishing principal. After this, the ABAC may be used for granting or preventing permissions according to attributes.
How to View Session Tags using CloudTrail?
CloudTrail can be utilized for viewing requests which were performed for the sake of assuming roles or federate users.
CloudTrail log file: Contains data regarding principal tags for this assumed federated user session or assumed-role.
Let’s suppose that you choose to perform an STS AssumeRoleWithSAML request, then you go ahead and pass session tags, and finally get the tags set as transitive.
You will get the below data in your CloudTrail log.
AssumeRoleWithSAML CloudTrail Log Example:
| “requestParameters”: { |
| “sAMLAssertionID”: “_c0046cEXAMPLEb9d4b8eEXAMPLE2619aEXAMPLE”, |
| “roleSessionName”: “MyRoleSessionName”, |
| “principalTags”: { |
| “CostCenter”: “987654”, |
| “Project”: “Unicorn” |
| }, |
| “transitiveTagKeys”: [ |
| “CostCenter”, |
| “Project” |
| ], |
| “durationSeconds”: 3600, |
| “roleArn”: “arn:aws:iam::123456789012:role/SAMLTestRoleShibboleth”, |
| “principalArn”: “arn:aws:iam::123456789012:saml-provider/Shibboleth” |
| }, |